This is what Mark Stocklin, a security researcher and "white" hacker at IBM's research center in Yorktown, said during a press visit to the company's research center in Zurich.
When Chris Sciacca, director of the communications and spokes department at IBM's research center in Zurich, entered, he discovered a message from hackers who had locked the computer and were demanding a ransom. So far, it's an old trouble. What is new in this attack is that the hacker pulled his picture from LinkedIn and ran an artificial intelligence system that compares the photographs of those who approach the computer and as soon as it was Sciacca, the system was locked.
Fortunately for Sciacca, the hacker was not a black hat hacker, but rather a cryptography and security researcher at the same lab named Mark Stocklin, who wanted to demonstrate what a hacker attack combined with artificial intelligence might look like.
Stocklin, a cryptography researcher and "white" hacker working at the IBM Research Center in Yorktown, illustrated this during a press tour of the IBM Research Center in Zurich in a video conference.
A targeted data attack is one of the greatest dangers for any organization and it is always at a disadvantage because the attacker has all the time and resources in the world to study the work processes in the organization to find a loophole. Can artificial intelligence be used to turn this arms race to the organization's advantage?
"Hackers have learned to take advantage of artificial intelligence"
"Hackers have learned to exploit artificial intelligence to increase the power of many malicious programs, as they look for ways to steal, monetize, destroy encrypted data, damage companies, destroy consumer trust, and harm business operations in ways that can even be life-threatening." Stocklin said.
According to him, "the scope of the attacks and the number of people they affect are also increasing. Almost 3 billion records were leaked in 2017. Sensitive information from many publicly disclosed events was later discovered when it was offered for sale on dark web markets."
"Furthermore, our teams have witnessed dozens of high-profile targeted attacks that have paralyzed the day-to-day operations of essential service providers, including shipping companies and hospitals. The attacks affected organizations around the world," he added.
“One of the most prominent targets of a targeted data attack is the attacker's ability to gain access to confidential internal systems, often to the point of abusing user-level or even administrator-level privileges. In addition, hackers are often able to gain read and write file system access privileges on sensitive or critical computer systems, and with a foothold on a targeted system, they may be able to gain almost unlimited file system exposure.” Stocklin explained.
"Another case where these permissions can be a problem is when software is installed legitimately at the same time as the access permissions of the user who runs it. This can be problematic when the software accidentally contains malicious code, or a benign-looking file that causes an exploit that can affect legitimate software (eg, productivity programs, web browser, etc.). In such cases, the adversary can obtain the user's inherent level of privileges and perform actions reserved only for authorized users," he said.
“Given these challenges, we question whether permission-based access control models for file systems are actually adequate for protecting data assets in today's threat landscape. Are there better ways to protect the data while placing an asymmetric advantage towards the defender?” added Stocklin.
"We believe the answer is yes. We recommend in our research a new type of file system that we consider to be a radically new system approach, called Files Decoy Systems (RTD Dcy DX), which complements access control schemes and can help overcome many of the fundamental limitations of traditional access control credentials," he added. .

the magic door
According to Stocklin, "We can take the attackers on a journey even without trying to understand what their intentions and abilities are. If we only block them we will not be able to identify new types of potential threats. The solution is that we transfer the risk to them. That's why we let them in, but do it in a controlled way. The litter box watches over them. It's a kind of separate world for them where we can examine how they try to fight our tactics - the defenders."
"We seemingly give them access to the file system, which looks like a real file system, and then we can create new files or replace the content of existing files," he added.
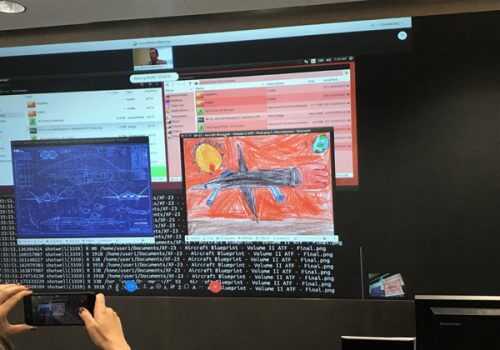
"At Luna Parkim there is a facility known as FUN HOUSE, where doors open and each door leads to other strange places. We imitate this phenomenon and build a FUN HOUSE for hackers. They break in, you place many doors for them, and they start opening all the doors and want to steal the contents of the files, but instead of the real file, we give them gibberish," he added.
In the presentation, Stocklin showed on one side a plan for building an airplane, which was the target of the burglars, and on the other side what they really got - children's drawings of airplanes. "This method can provide a good solution for ransomware attacks. The attackers will think that they are encrypting sensitive files that the user will be willing to pay a lot of money for, while what they attacked were dummy files.” Stocklin concluded.
More of the topic in Hayadan:
- "All cyber-physical devices will have to be safe and reliable and will be required to respect privacy"
- Cyber protection of space assets is a growing field. More and more satellite operators became aware of the risks
- Robots for remote analysis, and cyber risks - researchers hacked into remote analysis systems to illustrate the risk
