Cyber security will be of great significance to the way in which the general public views the use of these systems, in terms of safety and maintaining medical privacy and confidentiality.
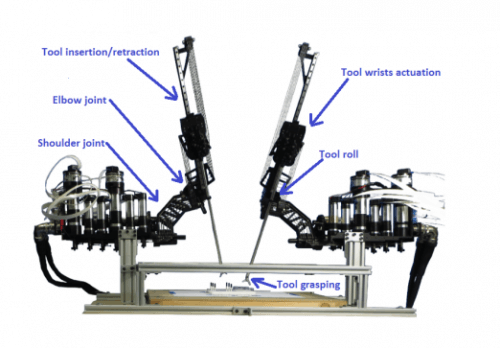
The number of robots for remote surgery, sold worldwide, increases by approximately 20% each year. The first surgery using this type of device was performed in 2001, and the benefit of this technology is of course the possibility to perform surgery by a specialist at a great distance from his place of residence, without the need for long trips, thus increasing his availability and the number of patients he will treat.
The first analysis was performed using an optical fiber specially installed for this purpose. Today, the communication between the robot and the control unit operated by the surgeon is done via the Internet, with a special protocol developed for this purpose (Interoperable Telesurgery Protocol). Also, the video image from the robot's camera is broadcast over the network. Today this communication is completely open, and in fact any surfer can watch it if he connects to the appropriate website.
Researchers from the University of Washington in Seattle examined the risk posed by a cyber attack on such a robot (including the control position), in light of the fact that today the system is not protected (and besides safety, there is also a lack of protection of privacy). They tried three types of attacks: delaying, rearranging and deleting commands and reports between the control station and the robot, changing commands that were sent or inserting ones that the surgeon did not intend, and finally taking complete control of the device. In all three methods, they succeeded in the attack without interruption. The degree of damage that can be caused by such a cyber attack can of course be fatal.
Perhaps surprising, but the technology to defend against most cyber attacks of this type exists and is proven, in various systems: military, financial and other - encryption and decryption, including the transmitted video signal. The application of this method can also provide an answer to privacy protection considerations. The operation times of the encryption and decryption software, by the way, are very fast and do not interfere with the real-time operation of the communication and the robotic system itself.
It should be noted that cyber security will be of great significance to the way in which the general public views the use of these systems, in terms of safety and maintaining privacy and medical confidentiality.
The researchers' article:
