Ukraine was prepared not only for the physical war being waged there, but also for cyber war. This explains, among other things, the request of the Ukrainian government from Elon Musk for modems for the Starlink space internet systems

By Omri Wexler, Senior researcher and cyber project manager At the Yuval Na'eman workshop, Explains the various cyber security aspects of the conflict in Ukraine.
Ukraine's vice president recently said the country has launched an 'IT army' to fight Russia in cyberspace. How would you rate Ukraine's cyber capabilities?
"Actually, so far several attempts have been made to assess the national cyber power of different countries, but Ukraine was not among them due to the lack of data. While the research community is still in the dark about Ukraine's cyberspace capabilities, we can assume that due to the fact that Ukraine has been the focus of Russian cyberattacks since the annexation of Crimea in 2014, their cyber defense teams should be highly experienced.
The Ukrainian government has called on the country's hacking community to help protect its infrastructure, conduct espionage and conduct disruptive activities against Russian forces. In addition, various international hacker groups have declared that they will act against Russian targets.
Screenshot from a popular St. Petersburg news outlet (https://www.fontanka.ru/): On February 28, several Russian news sites were attacked, warning readers against "sending sons and husbands to certain death." The 'Anonymous' group took responsibility
Who is behind the downfall of the official website of the Kremlin, the office of Russian President Vladimir Putin, kremlin.ru?
“The type of attack we see on Russian official websites is called a Denial of Service (or DDoS) cyber attack. This is a relatively easy task, and does not require sophisticated cyber expertise. When you look at previous cyber attacks attributed to Western governments, especially the American Cyber Command, it does not seem to be a case of Western retaliation (cyber attacks in the West would in theory look more like shutting down military systems and so on), but rather the work of "activists" - hackers who use their abilities as part of a hack Their social/political background. It could also be the work of Ukrainian hackers who used the opportunity to hit some symbolic target."
So it can be said that in this area the power is no longer in the hands of the state?
"This is true. There are many other actors with access to cyber capabilities of varying complexity. However, advanced abilities require resources, such as money and expertise. Therefore, the most capable threat actor in this regard is still the state. It is important to mention that cyber capabilities take factors such as population and geographic size out of the game, which are considered very vital when it comes to conventional military power.
I think in the current conflict, local or international hackers can mostly embarrass the Russian government and cause some disruptions. One of the ways that international hackers can cause damage to Russian targets is through ransomware attacks that encrypt data and thus make it unreadable to the systems that use it. Other damage could include the leakage of highly sensitive or classified data, which would be used by more sophisticated groups for more sophisticated attacks. However, the damage they may cause is generally limited compared to the capabilities of Western governments."
The Russian invasion disrupted Ukraine's internet connection, so the country managed to mobilize public opinion with the help of social networks, and its deputy prime minister, Mykhailo Fedorov, asked billionaire Elon Musk on Twitter to make available his company's Starlink satellite broadband service in Ukraine. Musk responded.
What kind of cyber operations were employed in this conflict?
"Prior to the military strikes, the Russians also used DDoS attacks and flooded Ukrainian government websites and banks. Other attacks included 'wipers', malware that erases data and renders computers unusable. There are many tools in the cyber toolbox."
What were the Russian goals of the cyber attacks?
"In January, there were some experts who claimed that the purpose of the attacks was to steal information relevant to the upcoming invasion. The DDoS attacks may have been used as a distraction, while the wiper attacks prevented the Ukrainian government from recovering quickly by wiping data and preventing machines from booting. The Russians also did their best to instill fear and doubt among Ukrainian citizens and embarrass the Ukrainian government. These attacks were accompanied by a constant disinformation campaign, which included reports of Ukrainian aggression in eastern Ukraine."
Did it work?
"There is no evidence that the attacks undermined public support for the Ukrainian government, inside or outside of Ukraine. It appears that some of the Russian disinformation was also directed at local Russian citizens, with the aim of increasing support for the attack. There is still no indication that it worked, because reports are coming from the field from Russian soldiers who say that they were forced to invade Ukraine."
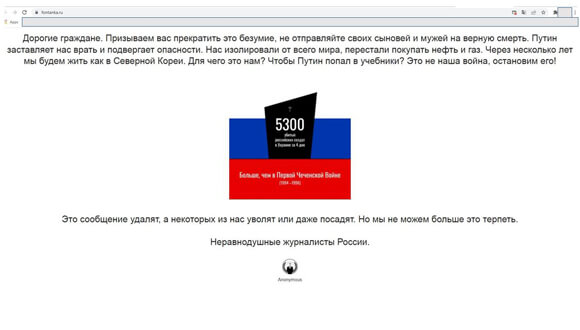
Screenshot from popular Russian news outlets: On February 28, several Russian news sites were attacked, warning readers against "sending sons and husbands to certain death." The 'Anonymous' group took responsibility
Should we expect more cyber attacks from Russia?
"I believe that Russian aggression in cyberspace will continue, mainly to support its military operations. It is very possible that we will continue to see cyber attacks that paralyze the power grid, water systems and other critical infrastructure, given the fact that many critical systems in Ukraine use Russian technologies and software. An excellent example is Ukraine's electricity grid, which was built during the Soviet Union. It is very likely that there is much more malware lying dormant on Ukrainian systems, ready to be deployed and activated.
Russian threat actors will likely direct their cyber efforts also against the member states of NATO and the European Union, as revenge for the support for Ukraine and the announcement of sanctions. In fact, banks, critical infrastructure operators, government agencies and public administration in Europe and the US have already been on alert for some time. Earlier this month, oil and fuel supply companies in Germany, the Netherlands and Belgium were hit by ransomware and forced to operate at limited capacity. These attacks were attributed to a Russian-speaking group called 'BlackCat', and given that what all these countries have in common is that they are NATO member states that agreed to send soldiers and aircraft to the countries surrounding Ukraine, it is difficult to separate these attacks from the crisis in Ukraine."
Will the West continue to sit on the sidelines?
"Besides sanctions, the West may launch cyber attacks. According to reports, US President Joe Biden was presented with various options for conducting cyber attacks aimed at disrupting the Russian invasion. UK Defense Secretary Ben Wallace has stated that the UK may launch cyber attacks on Russia if it targets UK networks. However, given their sensitive position, Western responses in cyberspace are likely to be limited. It really depends on the goals and the profit they want to achieve.
Theorists have long attempted to define how cyber offensive operations can be exploited within political and military conflicts, and whether they stand on their own or support conventional military operations. The Russian invasion of Ukraine and the preceding months, therefore, must be investigated as a CASE STUDY in order to understand the nature of cyberwarfare operations.
