Is the current generation of electronic encryption strong enough to protect your information online today? The American Standards Office thinks not
By Rui Weizfeld, MFA, Shawn Galantzan, MFA, Ofir Yosef, advisor to the security system
Advances in quantum computing and their strengthening of quantum computers already pose a challenge to the protection of information using electronic ciphers that are in use today - in a way that does not depend on their availability in the market, recent changes in the policy of the American government bring to light a significant change of perception in the field of information security.
The steps in realizing a digital cipher
Cryptography relies on solving "complicated" mathematical problems, these serve as a basis for performing digital signature operations, validation Authentication), distribution and encryption of information.
Diagram 1 describes the encryption process in an abstract manner in four central stages, the creation of the secret key, signing and verification of the key, its distribution and use to implement the encryption between the endpoints.
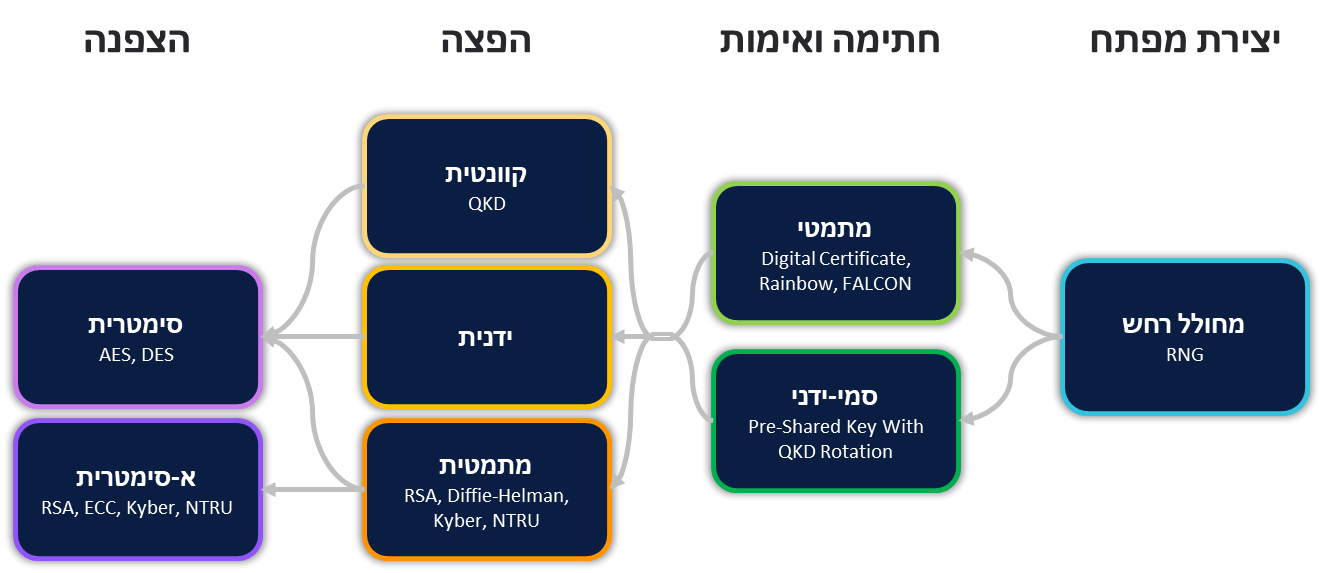
The key creation stage is based on a noise generator or RNG (Random Number Generator) whose function is to produce a sequence of numbers that cannot be logically or systematically predicted so that their strength is equal to the random chance in which they were generated. There are many options for noise cancellation from dedicated systems to cloud services public.
The digital signature and verification is a cryptography method that makes use of complex mathematical problems, in order to verify the key and ensure that its origin is authentic, there are several digital signature methods, among the most common are DSA adopted in 1993 by the United States government as a federal standard (FIPS) and RSA published in 1977 , among others, by scientists from the Weizmann Institute of Science.
Distribution (Key Distribution) is a general description of various methods dealing with the transfer, management and maintenance of secret encryption keys in a secure manner between two or more entities communicating in the network, this transfer is required in order to decipher the content of the encrypted messages, the distribution methods are based on complex mathematical calculation problems, The most common ones are RSA and Diffie Hellman proposed in 1976.
The key enables the implementation of encryption, whether in a symmetrical way in which the encryption algorithm uses a single encryption key for example in the common encryption method AES or in an asymmetric way, in which the encryption key is different from the decryption key and they exist as an exposed public key and a private key that is kept secret and used for decryption respectively.
Prominent use cases of encryption keys
We will divide the use of the cipher into two main uses - the first, protection of the data communication infrastructure and the second, secure access to services through an internet infrastructure, these uses have many aspects such as protecting the confidentiality of the information and increasing the immunity of the communication equipment to attack from the communication medium itself.
Protection of the communication infrastructure is implemented through a combination of dedicated protective protocols such as MACSec and IPSec, which use a key and symmetric encryption methods in order to create secure channels through the communication infrastructure that aims to provide protection against impersonation, shutdown, information leakage and the confidentiality of the information itself.
Another use of the cipher is in secure access over an Internet infrastructure (or PKI infrastructure) to a wide range of services and endpoints such as IoT devices, cloud computing, mobile devices and for the performance of identification verification - these are usually applied to the TLS (or TLS/SSL) protocol in The Internet is widely used and is supported by most modern browsers.
The PKI infrastructure (Public-key infrastructure) is based on hardware and software and the implementation of information security policies and processes used to manage, distribute, use, store, and retire digital certificates.
The use is usually made by asymmetric protocols, the public key is transmitted by the visible internet infrastructure, on the decoder side a private key is used that is kept in a secure manner.
When working with a public infrastructure, such as cloud computing, HSM components (Hardware Security Modules) are used to perform cryptographic processing and to keep the key securely, as described in Figure 2.
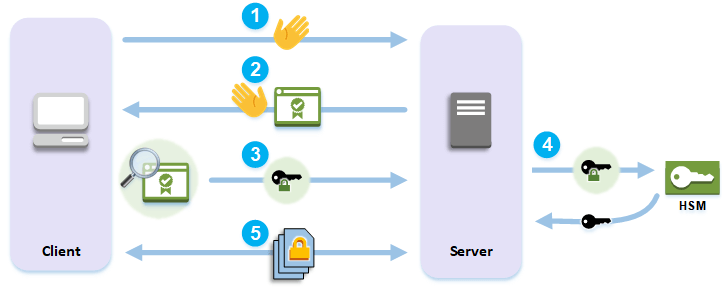
After the creation of an unencrypted communication channel between the end units, the source of the digital signature is verified and the public key is extracted from it, later on this basis a secret is produced that is encrypted using the same public key - the possibility of decryption is limited to the party holding the private key or the result of breaking the cipher.
Quantum computing
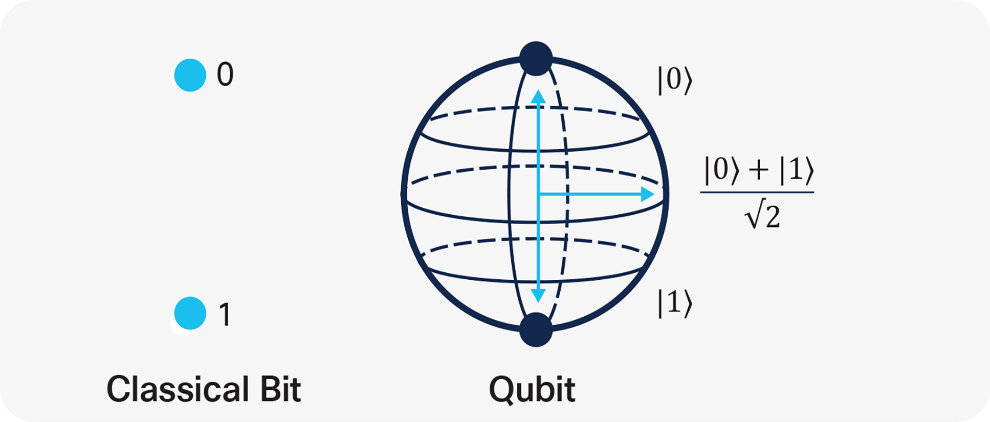
Quantum computers use qubits ((quantum bits) as a basic unit of information, individual qubits can be represented in a binary base of 0 or 1 (classical bits), but they can also be in any state between 0 and 1, the position of the qubit between the states is Probabilistic.
This probability is defined by the principle of quantum superposition, thereby enabling the activation of a series of complex manipulations (quantum algorithms) that allows a fast running time and resetting of uninteresting probabilities.
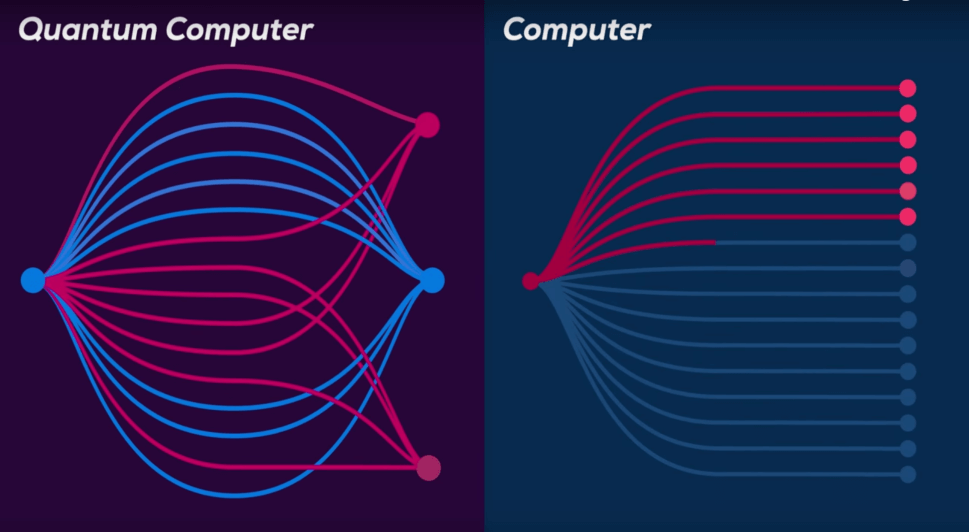
A graphic illustration of the use of the principles of quantum mechanics to realize parallel computation
The use of a quantum computer makes it possible to overcome the limitations and barriers of current computers in terms of memory and calculation power, this is made possible by the parallel calculation of several inputs and "interweaving" that preserves a reciprocal relationship (correlative relationship).
The correlative relationship between the qubits exists thanks to quantum entanglement, which is another basic principle of quantum mechanics, meaning that applying an action to one of the two qubits will change the state of the other, the realization of this principle and the principle of superposition, among other things, allow the calculation of Several simultaneous states on several qubits.
The post-quantum threat - why now and not in a decade?
A combination of various factors including the results of theoretical tests, such as the one described in the algorithm bull, and the great interest and real progress in the field of quantum computing that is expected to be realized in the foreseeable future To the eye Robust and broad has attracted the attention of standardization organizations and cyber agencies including NIST, the NSA and ETSI.
These organizations have issued serious warnings that the implementation of quantum algorithms, based on quantum computers, will require protection of communication and information exchange to deal with them, among these organizations NIST stands out, which has been holding a competition since 2016 which is expected to end this year and aims to standardize post-quantum encryption protocols as a replacement for those that exist today and are exposed to the threat posed by quantum computers.
in March 2022 Was published The instruction by the NCSC (NATO Cyber Security Center) and at the same time by the American government to update the defense systems so that they support the cipher defined by NIST as post-quantum, as well as immediate identification (180 days from the publication of the instruction) must identify and create a migration plan for systems that are not are in compliance with the post-quantum cipher as approved by the NSA.
This statement is dramatic as it brings to light a serious problem concerning the information stored today. If the communication channels are being listened to today, secret information is recorded through it - all that remains is to wait for the realization of a quantum computer in the future that will allow overcoming the existing cipher, most of which has not been defined by the various standardization bodies as post-quantum.
At the same time, the University of Cambridge Has released In recent months, (where, among other things, the NIST study from 2016 takes place) that leading mathematical algorithms intended to be used as post-quantum verification and distribution methods have been weakened by classical computers.
Quantum distribution - what is it anyway?
QKD or Quantum Key Distribution is used as a method for exchanging and distributing keys, based on physical principles from quantum mechanics, the principle of use is based on the joint creation of a symmetric private key between the two parties using quantum and classical channels (optical fibers or wireless channels).
QKD can be implemented using the BB84 protocol, which uses polarized photons, the bits used by the key are encoded on two polarization bases (diagram 7) of photons that maintain an uncertainty ratio between them, a measurement of one of the bases will cause the noise in the other feature to increase.
If these keys (=qubit) are intercepted by a listener (=measurement) in the optical medium, the qubit will realize a probabilistic change in its state and as a result will destroy the key and allow detection of the listening attempt.
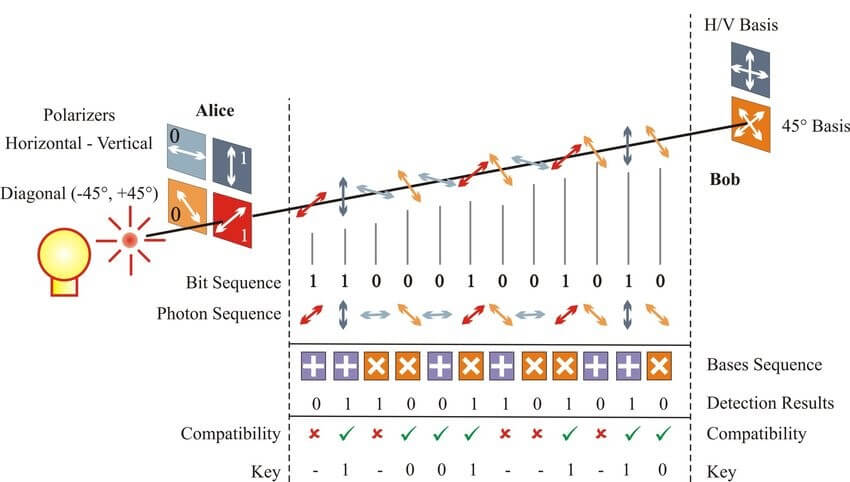
An implementation of the BB84 protocol, along with other protocols in the field of quantum distribution, was demonstrated in the 2000s as a post-quantum-less distribution security solution.
How is quantum distribution realized?
Realization of QKD is possible in two main ways, the first is through the optical infrastructure itself which allows the use of dedicated wavelengths to exchange the keys through a quantum channel or through the use of a wireless medium (Free-Space) which uses microwave systems, cellular, satellite or airborne platforms.
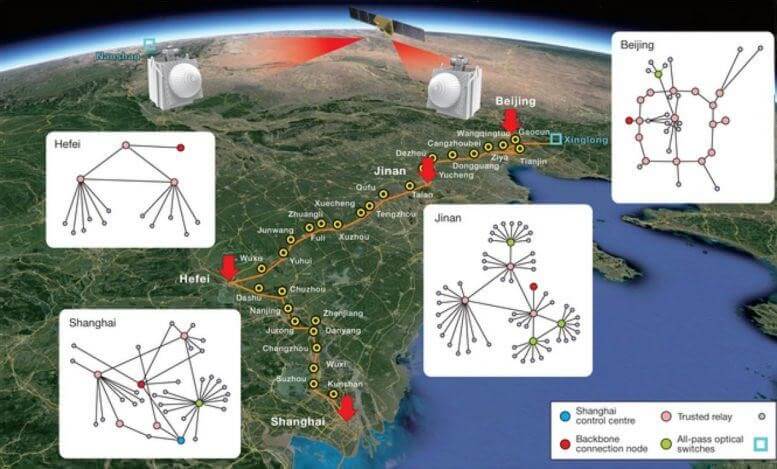
The distribution of the key will allow its transfer between the subscribers who maintain quantum communication between them, this will establish a kind of "quantum backbone" that will allow endpoints where it is possible to receive an authenticated key in a secure manner that meets the immunity requirements from a post-quantum system directly or by charging an external device (DOK or laptop ), communication components (data communication networks) on the highway route will "benefit" from the keys to implement their cipher among themselves for the purpose of protecting the communication infrastructure or the confidentiality of the information on the route.
But the significant application is the possibility of realizing the secure key obtained "from the quantum avenue" as part of the SSL/TLS mechanism, on an Internet infrastructure and in front of public cloud servers, in that the relative advantage of a corporate noise generator is preserved in a way that enables post-quantum immunity even when it is distributed and verified to Against public applications outside the boundaries of the organization.
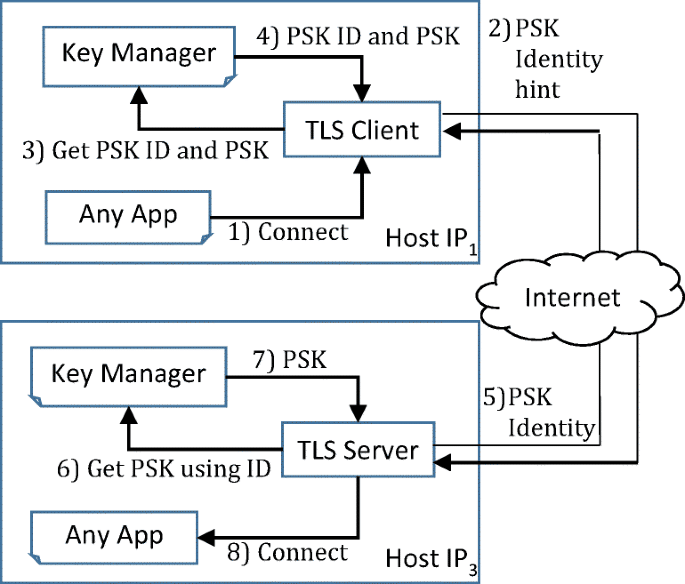
Figure 7 describes a system that implements a TLS server for cloud applications and public services, the server receives the key on a secure website with high reliability and through it accessibility to the public infrastructure is enabled.
Integration of the HSM component (Hardware Security Module) It will make it possible to increase the level of protection of the solution, where the encryption keys will be managed and additional verification will be possible with the end users.
Networks Blockchain As another use case
Another innovative implementation of encryption keys that use quantum distribution is for distributed networks (Blockchain), this use was demonstrated in the banking companyJPMorgan , in which quantum distribution is used to protect against citation in the Blockchain network by an optical channel.
In the article From 2021, another application of this method is described at the Inter-American Development Bank, in which the quantum distribution channel is used to provide keys for the bank's public services. The use of keys enables overcoming the post-quantum challenges and the classic authentication challenges that exist in the cryptographic channels based on TLS that the banks use. Today, use enables greater application of quantum distribution methods and the ground for greater commercial adoption.
The understanding of the implementation of the electronic protection methods as they exist today in the free market can be exposed to future validity. Many entities have realized that even though their communications are encrypted, it is worthwhile to act and change the encryption methods so that they are protected against a future quantum threat. We are seeing the budding of relevant uses of quantum communication for key distribution in a way that would enable hermetic protection against future attacks.
More of the topic in Hayadan:
- Researchers have developed a new device that will allow protection against quantum cracking
- Researchers are expanding the use of deep learning to distinguish ciphertext from random noise
- Emirati researchers test the promise and limitations of a Ben Gurion researcher's algorithm for cracking encryption
- "Any device built today that is not compatible with quantum encryption will be a hack, and a car is a good and dangerous example"
- There is an option for safe encryption - quantum encryption

3 תגובות
The writers are very understanding and certainly not reciting.
So far, all the methods proposed as a replacement for QKD have been hacked. Someone will always come up with something new that hasn't been hacked yet, but it's worth waiting to understand if it's actually durable.
Regarding the man in the middle attack, we would be happy for the learned commenter to base his opinion. The bb84 protocol certainly provides a proper answer to this issue.
It is obvious that the writers do not understand and are only reciting. The replacement for rsa and elliptic curves will be lattice-based cryptography and soon there will be a suitable standard.
The qkd is an academic protocol with a quantum touch but without any advantage in the practical world and does not stand up to a man in the middle attack.
exciting! Quantum computing is an important subject with great potential.
Very interesting article. Thanks.